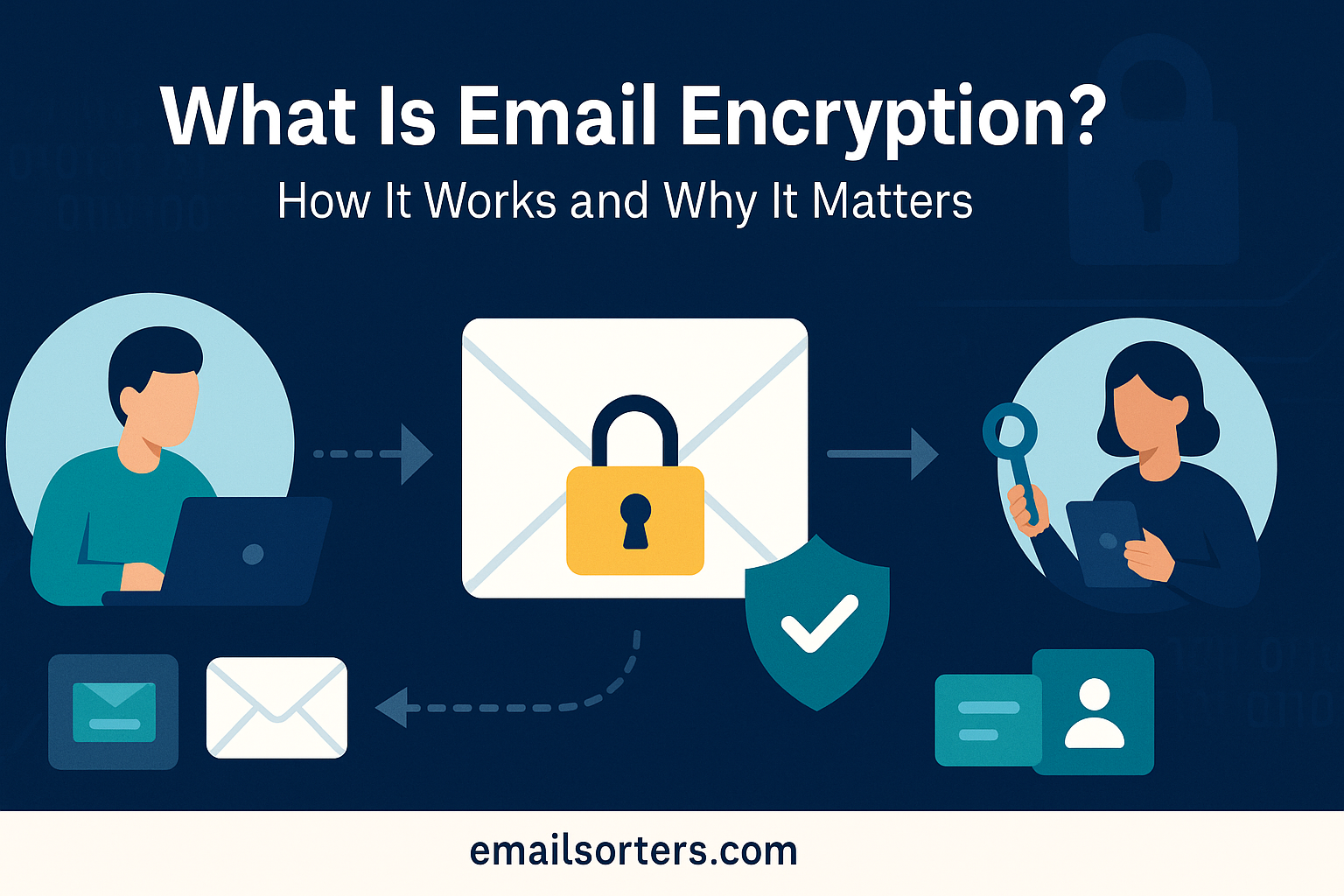
Email encryption is the process of converting the contents of an email into unreadable code to prevent unauthorized access during its transmission. This ensures that only the intended recipient, who has the correct decryption key, can read the message. In simpler terms, it locks your email with a digital key before sending it and ensures that only the right person has the matching key to unlock it.
The main purpose of email encryption is privacy. When you send an unencrypted email, it can potentially be read by anyone who intercepts it, whether that’s a hacker, an ISP, or even government surveillance. Encryption protects against this by securing your messages from point A to point B. It’s a critical component of Email Security, especially in today’s digital world where sensitive data travels constantly over the internet.
As email becomes more integral to professional and personal communication, encrypting your emails is not just a good idea, it’s a necessary measure to protect identities, business secrets, legal documents, and financial data. For individuals, it guards against scams and identity theft. For businesses, it can mean the difference between client trust and a devastating data breach.
Types of Encryption: End-to-End vs. Transport Layer
There are two main types of email encryption: End-to-End Encryption (E2EE) and Transport Layer Security (TLS), also known as in-transit encryption.
End-to-End Encryption ensures that the content of an email is encrypted from the sender to the recipient. Not even the email service provider can read the message. This method uses public and private key pairs where only the recipient can decrypt the message using their private key. PGP and S/MIME are the most common forms of end-to-end encryption.
Transport Layer Security, on the other hand, encrypts the email as it moves between servers. While this protects against interception during transmission, the email is accessible in readable form on both the sender and recipient’s mail servers. Gmail and Outlook, for example, use TLS by default.
While TLS is suitable for casual correspondence, end-to-end encryption is essential for truly private communication. Understanding the difference helps you choose the right level of security for your needs.
How Email Encryption Works
The Encryption Process Step-by-Step
To grasp how email encryption works, it helps to understand the lifecycle of a message from sender to recipient. When you compose an email and send it through an encryption-enabled client, the content is transformed into ciphertext using an algorithm. This ciphertext appears as a string of gibberish to anyone who doesn’t have the proper key.
Here’s a simplified version of the process:
- You write your message and click send.
- The email client uses the recipient’s public key to encrypt the message.
- The encrypted message is transmitted over the internet.
- The recipient receives the email and uses their private key to decrypt it.
- The message appears readable only to the intended recipient.
This encryption process ensures that even if someone intercepts the message mid-transit, they can’t read its contents without the private key. These encryption protocols also ensure the message isn’t altered in transit, preserving the integrity of the information.
Role of Public and Private Keys
At the heart of most email encryption systems is a mechanism known as public-key cryptography. This system uses a pair of keys: one public and one private.
The public key is shared with anyone who wants to send you an encrypted message. The private key is kept secret and used to decrypt the message. When someone sends you an email using your public key, only your private key can unlock it. This two-key system ensures that even the sender cannot decrypt the message once it’s sent—only the intended recipient has that ability.
This method not only secures the message but also confirms the identity of the sender, especially when combined with DMARC Record checks and digital signatures. These cryptographic principles are the backbone of secure communications today.
Why Email Encryption Matters in 2025
Preventing Unauthorized Access
As cyber threats become more sophisticated, the risk of someone intercepting your email has never been higher. From corporate espionage to data harvesting by cybercriminals, the threats are real. Without encryption, every email you send is like a postcard—it can be read by anyone who handles it on its journey.
In 2025, as more of our communication includes sensitive data—contracts, tax records, bank details—the need to prevent unauthorized access is more urgent than ever. Encryption shields this data from prying eyes, offering a simple but powerful way to protect personal and professional privacy.
Even if an attacker gains access to an email server or intercepts traffic over an insecure network (like public Wi-Fi), they cannot decipher an encrypted message without the correct decryption key. That’s why encryption is considered the last line of defense in digital communication.
Protecting Sensitive Information and Identities
Email encryption is not just about security—it’s also about preserving trust. Businesses that fail to secure sensitive information can suffer reputational damage, legal penalties, and customer attrition. For professionals in fields like law, healthcare, and finance, sending unencrypted information can violate privacy laws and regulatory requirements.
Encryption also protects against Email Spoofing, where attackers forge the sender’s address to impersonate a trusted party. Combined with email authentication measures like SPF, DKIM, and DMARC, encryption strengthens identity verification and guards against phishing.
In personal contexts, encryption keeps your location, attachments, and private conversations out of reach from surveillance or misuse. As digital identities become more valuable—and vulnerable—protecting them through email encryption becomes essential.
Common Threats to Unencrypted Emails
Man-in-the-Middle Attacks
One of the most prevalent threats to unencrypted emails is the man-in-the-middle (MITM) attack. In this scenario, a hacker intercepts the communication between the sender and recipient, often by exploiting unsecured public networks or vulnerable email servers.
Without encryption, the attacker can read the entire contents of the email, modify it, or inject malicious links. This is especially dangerous for users who send login credentials, payment information, or confidential documents via email.
MITM attacks often go undetected, making them particularly insidious. Encrypting email data effectively neutralizes the threat, since intercepted content appears as indecipherable code to the attacker.
Email Spoofing and Data Breaches
Email Spoofing is another major threat to unprotected email systems. Attackers forge headers to make an email appear as if it’s coming from a trusted source. This tactic is used extensively in phishing campaigns and business email compromise scams. Unencrypted emails can be more easily spoofed, manipulated, or redirected without detection.
A spoofed message may trick recipients into revealing sensitive data, downloading malware, or transferring funds to fraudulent accounts. Encryption, alongside Two-Step Authentication, plays a crucial role in verifying sender identity and ensuring that communication remains confidential.
Data breaches resulting from exposed emails can have catastrophic consequences. Names, passwords, bank details, and personal messages can be leaked, sold, or used in identity theft schemes. Encrypted email systems reduce the risk significantly by making stolen data useless without the proper decryption key
Popular Email Encryption Protocols and Standards
S/MIME (Secure/Multipurpose Internet Mail Extensions)
S/MIME is one of the most widely adopted standards for email encryption and digital signatures, especially in corporate environments. It uses a centralized system of certificate authorities (CAs) to issue and manage encryption keys. These certificates verify the sender’s identity and enable encryption using public-key cryptography.
S/MIME is natively supported by most major email clients like Microsoft Outlook, Apple Mail, and Gmail (with enterprise setups). When you send an S/MIME-encrypted email, it uses the recipient’s public key to encrypt the message. Upon receipt, the recipient’s private key decrypts the content.
In addition to confidentiality, S/MIME provides authentication through digital signatures. This ensures that the email wasn’t altered in transit and confirms that it was indeed sent by the verified sender. For regulated industries that require audit trails and verifiable identities, S/MIME is often the go-to solution.
However, managing certificates across large teams can become complex. Expiring certificates, compromised keys, and central authority requirements make S/MIME less flexible for some users compared to open standards.
PGP (Pretty Good Privacy) and OpenPGP
PGP, and its open-source version OpenPGP, offer another powerful method of encrypting email. Unlike S/MIME, PGP operates on a decentralized trust model, often referred to as a “web of trust.” This model gives users more control over who they trust to exchange encrypted messages.
Users generate their own key pairs and share their public key manually or through key servers. Anyone with your public key can send you encrypted emails, and only your private key can decrypt them. PGP also enables users to sign messages, verifying both the sender and the message’s integrity.
One major advantage of PGP is flexibility. It works across multiple email platforms and doesn’t require corporate infrastructure or centralized authorities. However, this also means it demands more technical know-how from the user. Configuring PGP clients, managing keys, and verifying signatures can be a barrier for casual users.
Popular tools like Gpg4win (for Windows), ProtonMail, and Thunderbird with Enigmail make PGP more accessible. Despite its complexity, PGP remains a trusted solution for journalists, activists, developers, and privacy-conscious users.
Email Encryption vs. Two-Step Authentication
Complementary Roles in Security
Email encryption and Two-Step Authentication (2FA) are both essential components of email security, but they serve different purposes. Encryption protects the content of the message, while 2FA secures access to your email account.
Encryption ensures that your emails are unreadable to anyone except the intended recipient, even if they are intercepted. Meanwhile, 2FA prevents unauthorized users from logging into your account by requiring an additional verification step—like a code sent to your phone or an authentication app.
These two technologies work best when used together. Even if your email content is encrypted, it does little good if a hacker can simply log into your account and read your messages. Likewise, even the strongest 2FA won’t protect the content of your emails if they are sent unencrypted.
Implementing both gives you layered protection: encryption keeps the data secure, and 2FA ensures only you have access to that data.
For more about securing access, visit Two-Step Authentication.
When to Use Each and Why
You should use encryption whenever you’re sending sensitive data—financial documents, legal contracts, medical records, or personal identifiers. For professional users, this is non-negotiable. Even for casual users, encryption adds peace of mind, especially when communicating over public networks.
Two-Step Authentication should be used at all times, regardless of whether your emails are encrypted. It protects your entire email ecosystem, including drafts, saved messages, contacts, and synced data.
In a security-first environment, email encryption and two-step verification aren’t competing solutions—they are essential teammates.
How to Send Encrypted Emails
Using Built-in Encryption in Gmail, Outlook, etc.
Major email platforms like Gmail and Outlook have made it easier than ever to send encrypted messages, though the level of encryption varies by plan and configuration.
Gmail, for instance, uses TLS by default when communicating with other providers that support it. If you’re using Google Workspace (formerly G Suite), you can enable S/MIME for stronger, end-to-end encryption, though this requires certificate setup and administrative controls.
Microsoft Outlook also offers built-in S/MIME support. Once certificates are installed, you can digitally sign and encrypt messages with a single click. Office 365 Enterprise users can also use Microsoft Purview Message Encryption, which allows for flexible control and message expiry.
Apple Mail supports S/MIME natively, and users can install certificates to enable encryption and digital signing for each email account.
These platforms often show a padlock icon or a security message in the email header to indicate encryption status. However, unless you’ve configured S/MIME or PGP, your messages may only be encrypted during transmission—not end-to-end.
Third-Party Encryption Tools
If your email client doesn’t support advanced encryption, or if you want stronger security, third-party tools provide an excellent alternative. Platforms like ProtonMail, Tutanota, and Mailfence are designed from the ground up for end-to-end encrypted communication.
These services typically encrypt the message in your browser before sending and store it encrypted on their servers. Only the intended recipient can decrypt it using their credentials or private key. ProtonMail even allows you to send encrypted emails to users outside its platform by setting a shared password.
Desktop tools like Gpg4win for Windows or GPG Suite for macOS let you integrate PGP encryption with standard email clients. These solutions offer more control but require manual key management.
Whichever method you choose, the goal remains the same: secure your communications from start to finish, and ensure that only the intended recipient has access to your message.
Verifying Encrypted Email Senders
Verification Email — Meaning, Examples, and Best Practices
When dealing with encrypted emails, it’s crucial to ensure the message is truly from who it claims to be. This is where verification emails come in. A verification email is typically sent as a confirmation message to a user who signs up for a service, requests a password reset, or enables two-step authentication. It confirms identity, ownership, and often includes a unique verification link or code.
In the context of encrypted email, verification takes on an additional role—it helps establish that the person or service sending the encrypted message is legitimate. Best practices include clearly identifying the sender, providing traceable contact information, and using domain authentication to prevent impersonation.
For users, always scrutinize verification messages. Look for clear sender details, familiar domain names, and encryption indicators (like signed messages or padlock icons). If a verification email seems suspicious or unencrypted, avoid clicking on any links until you confirm its legitimacy.
Using DMARC, SPF, and DKIM
To effectively verify email authenticity, especially with encrypted messages, email administrators should implement DMARC, SPF, and DKIM. These DNS-based technologies work together to ensure that emails are coming from verified servers and haven’t been tampered with during transmission.
SPF (Sender Policy Framework) allows domain owners to specify which IP addresses are authorized to send emails on their behalf. DKIM (DomainKeys Identified Mail) attaches a cryptographic signature to each outgoing email, which the recipient can use to confirm it wasn’t altered. DMARC (Domain-based Message Authentication, Reporting & Conformance) builds on both SPF and DKIM, telling receiving servers how to handle messages that fail authentication checks.
DMARC also enables reporting, giving domain owners visibility into who is using (or misusing) their email domain. This is critical for preventing Email Spoofing, a tactic where attackers forge headers to impersonate legitimate senders.
How to Know If Your Email Is Encrypted
Visual Indicators in Email Clients
Most modern email clients make it fairly easy to see whether a message is encrypted—if you know what to look for. In Gmail, a small lock icon next to the recipient’s name indicates the use of TLS encryption. If you’re using S/MIME, Gmail will show a more detailed indicator with verification of the certificate.
Microsoft Outlook uses padlock symbols as well and allows you to view certificate details by clicking on the icon. On Apple Mail, encrypted messages often display a blue padlock when using S/MIME. If a message is signed but not encrypted, you may see a checkmark instead.
These visual indicators give users confidence that the message is secure. However, just because TLS is active doesn’t mean the email is end-to-end encrypted. For that level of assurance, you’ll want to see signs that PGP or S/MIME encryption is in place, meaning the message was encrypted before sending and can only be decrypted by the intended recipient.
Always double-check these signs, especially when handling sensitive information. Lack of encryption indicators should be a red flag when receiving high-value or confidential messages.
Email Headers and Metadata
If you want to dig deeper, you can inspect the email headers for technical confirmation. Headers contain metadata like encryption protocols, authentication results, and the route taken by the email. Look for terms like TLS, X-DKIM-Result, or Authentication-Results to assess the security measures applied.
For example, if a message contains the line Received: from … by … with ESMTPS, it indicates that the message was sent using TLS encryption. If DKIM passed, you’ll see a header confirming it along with the domain used.
While not every user will check headers, for professionals and IT teams, it’s an essential way to verify encryption status and trace suspicious messages.
Encryption in Professional Settings
Legal, Financial, and Healthcare Requirements
In regulated industries, email encryption isn’t optional—it’s mandated by law. For healthcare providers in the U.S., HIPAA regulations require encryption for any electronically transmitted patient data. Similarly, financial institutions must adhere to standards like PCI DSS or FINRA, which enforce strict controls over how client data is shared.
Legal firms, insurance providers, and educational institutions must also protect client or student data under privacy laws like GDPR in Europe and CCPA in California. In all these sectors, failure to encrypt sensitive information can lead to steep penalties, lawsuits, or loss of licenses.
In these environments, encryption is often paired with access control systems, audit logging, and third-party compliance tools. IT departments must regularly test encryption protocols, manage certificate lifecycles, and enforce authentication policies to ensure consistent protection.
The stakes are high, which is why these industries have been early adopters of robust email encryption solutions.
Small Business and Freelance Use Cases
Even outside regulated sectors, small businesses and freelancers handle sensitive data daily. Whether it’s a signed contract, a tax document, or a new product proposal, encrypted email protects intellectual property, privacy, and trust.
Freelancers and consultants often collaborate across borders and industries. Without IT teams to handle security, they must rely on accessible, reliable encryption tools like ProtonMail, Tutanota, or encrypted plugins for Gmail and Outlook.
Encrypting communications builds client confidence and shows professionalism. It also protects your work and correspondence from being intercepted or misused. For any self-employed person or small firm, taking the time to set up email encryption is a practical step toward long-term data protection.
Benefits and Limitations of Email Encryption
What It Protects
Email encryption primarily protects the content of the message from being read by anyone other than the intended recipient. It also guards attachments, metadata (in some cases), and even the sender’s identity if end-to-end encryption is implemented.
Encryption prevents eavesdropping on unsecured networks, ensures confidentiality during message transmission, and authenticates the sender’s identity when digital signatures are used. It adds a critical layer of defense in both personal and business communication, especially when dealing with contracts, credentials, or confidential reports.
What It Doesn’t Cover
Despite its power, email encryption has limitations. It does not protect against malware embedded in email content, phishing attempts using legitimate sender addresses, or human error—like sending a message to the wrong recipient.
Additionally, metadata like timestamps, subject lines, and routing paths are often not encrypted even when the message body is. This means some information is still visible to email servers and network intermediaries unless advanced encryption systems are used.
Finally, encryption is only as strong as its implementation. Poor key management, outdated algorithms, or relying solely on transport-layer encryption can all create vulnerabilities. That’s why encryption should be part of a broader Email Security strategy that includes anti-phishing, spam filtering, and authentication tools.
Email Encryption and Broader Email Security
How Encryption Fits Into Email Security — Guide to Stay Protected in 2025
Encryption is a foundational pillar of a larger email security framework. It plays a vital role in ensuring the confidentiality and integrity of email communication, but by itself, it’s not a complete solution. In 2025, with cyber threats growing more advanced, combining encryption with other security strategies is the only way to ensure comprehensive protection.
Modern email security involves layers: anti-malware scanning, spam filtering, sender verification, and behavioral analytics—all working alongside encryption. While encryption keeps your messages unreadable to outsiders, tools like anti-phishing filters and intrusion detection systems prevent malicious content from reaching your inbox in the first place.
Another layer is access security, like Two-Step Authentication, which protects the endpoints—your devices and login credentials. Paired with DMARC, SPF, and DKIM, encryption helps form a robust barrier against threats such as impersonation, Email Spoofing, and credential theft.
For businesses and individuals alike, relying solely on encryption without these other measures is like locking your front door but leaving your windows wide open.
Pairing Encryption with Anti-Spoofing and Authentication
Encryption can protect your email’s contents, but verifying who sent that email and whether it’s trustworthy is another challenge. This is where anti-spoofing protocols come into play. By setting up DMARC, SPF, and DKIM, domain owners can authenticate their messages, making it harder for attackers to forge their identity.
For example, even if an attacker sends a seemingly encrypted email, without DMARC in place, recipients have no way of confirming its legitimacy. Conversely, authenticated but unencrypted emails are still vulnerable to interception. Only when encryption is combined with sender authentication do you achieve both confidentiality and trust.
Many encryption-capable email clients also verify digital signatures—cryptographic proofs that the sender is who they say they are. This not only deters spoofing but also helps prevent modified or malicious messages from reaching unsuspecting users.
In 2025, pairing encryption with sender verification isn’t optional—it’s expected. It’s the combination of these tools that makes modern email systems both private and trustworthy.
Conclusion
Email encryption is no longer a tool just for tech-savvy users or secretive organizations—it’s a practical necessity for anyone who values privacy, security, and digital trust. From the boardroom to the freelancer’s home office, encryption protects sensitive information from interception, manipulation, and misuse.
As cyber threats evolve, encryption acts as your first line of defense, transforming readable messages into scrambled code that only the intended recipient can decode. But encryption doesn’t work in isolation. To be truly effective, it must be combined with authentication protocols, two-step verification, and vigilant email management practices.
Whether you’re a casual email user or a professional handling client data, taking steps to encrypt your emails is one of the smartest moves you can make in today’s digital world. It protects your information, your identity, and your peace of mind.
FAQs
Is email encryption necessary for everyday users?
Yes, especially if you’re sharing personal information like addresses, financial data, or health details. While casual users may not need full end-to-end encryption every day, enabling TLS encryption and using secure email services provides essential protection.
Can encrypted emails be hacked?
Encrypted emails are extremely difficult to hack without access to the recipient’s private key. However, if the key is compromised or if poor encryption algorithms are used, the message may be vulnerable. Proper key management is critical.
How do I encrypt my emails for free?
You can use services like ProtonMail or Tutanota, which offer free end-to-end encrypted email accounts. You can also install plugins like Mailvelope for Gmail or use GPG tools for desktop clients.
Do all email services support encryption?
Most major services support encryption in transit via TLS, but not all offer end-to-end encryption. For full encryption, choose providers that support S/MIME, PGP, or offer native E2EE.
What’s the difference between SSL/TLS and end-to-end encryption?
SSL/TLS encrypts emails during transmission between servers but not on the sender’s or recipient’s end. End-to-end encryption scrambles the message at the source and decrypts it only on the recipient’s device, ensuring complete privacy.