Two-step authentication protects your accounts even if someone steals your password. It adds a second layer of security, fast, simple, and powerful.
Imagine getting a login alert from a city you’ve never been to. Your password is no longer enough. That second step? It can stop a hacker cold.
This small step makes a big difference. It keeps your emails, bank info, and social apps safe from unauthorized access.
In this quick guide, you’ll learn how two-step authentication works, why it matters, and how to turn it on in just a few minutes.
Let’s lock down your digital life, starting now.
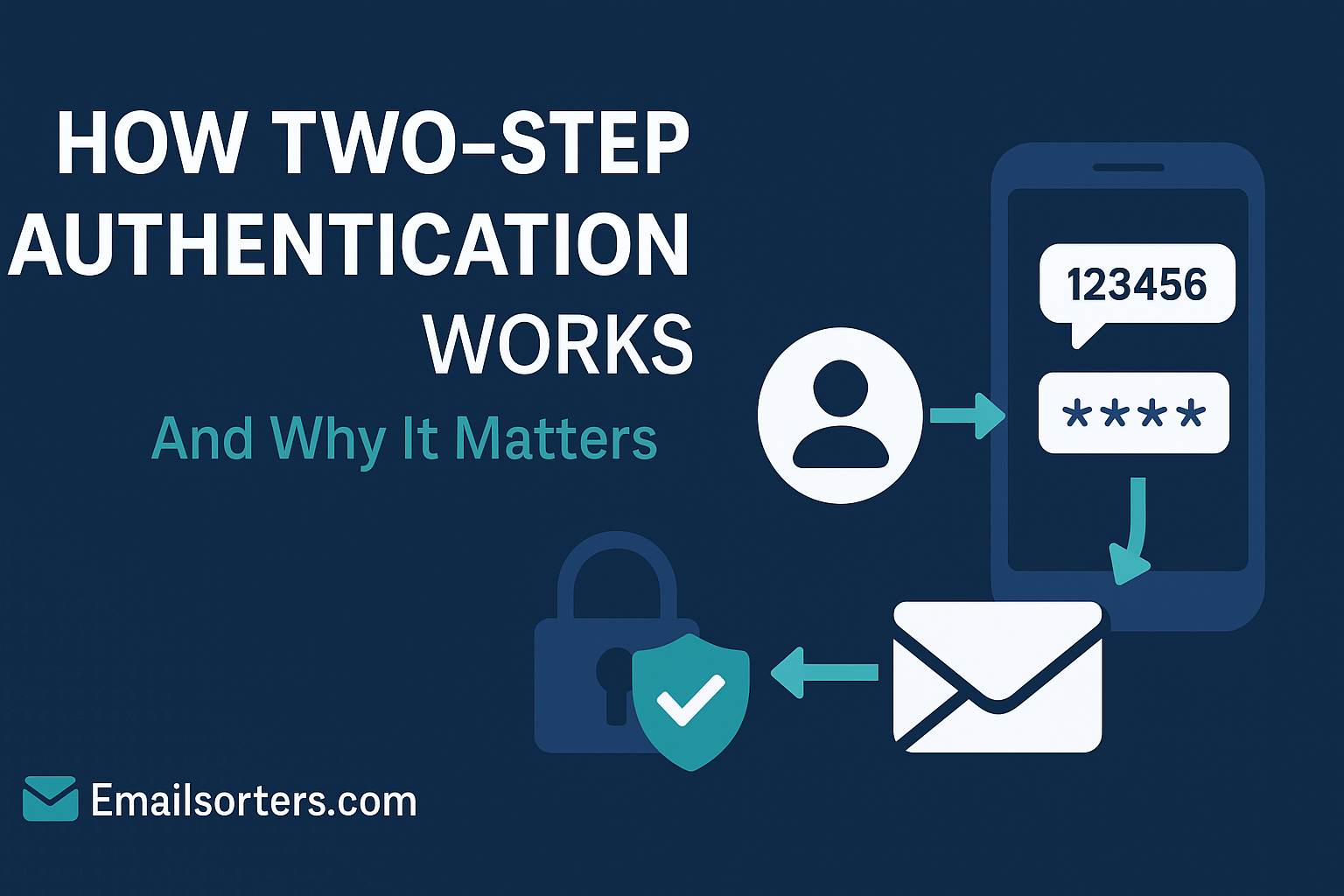
What Is Two‑Step Authentication
Two‑step authentication is a security process in which a user provides two separate forms of identification before gaining access to an account. The first is usually something the user knows—like a password. The second is something the user has—like a mobile device, email code, or biometric trait.
The idea is simple but powerful: even if an attacker gets hold of your password, they can’t access your account unless they also have access to your secondary device or identity factor. This system dramatically reduces the success rate of data breaches, phishing, and brute‑force attacks.
Unlike single‑step login processes, two‑step verification adds a layer of defense by ensuring that both your knowledge and your possessions are required for entry. It doesn’t stop hackers from trying, but it significantly raises the bar for success.
Difference Between 2FA and Two‑Step Authentication
Although the terms are often used interchangeably, two‑step authentication and two‑factor authentication (2FA) have a subtle distinction. Two‑factor authentication typically involves two distinct types of factors (something you know and something you have), while two‑step authentication may involve two of the same type (e.g., password + email code, both knowledge-based).
In practical terms, both systems achieve a similar goal: they protect your data using a layered approach. The difference matters more in technical conversations than it does in everyday use.
Some security frameworks insist on true two‑factor setups to avoid weak secondary verification, while others consider two‑step authentication a sufficient middle ground for most users.
Why Two‑Step Authentication Matters for Security
Protection Against Common Threats
Cybercrime is on the rise, and passwords alone are no longer strong enough to protect sensitive data. With massive data leaks from major services like LinkedIn, Adobe, and Facebook, billions of passwords are now floating around the dark web. Even strong passwords can be compromised through phishing attacks, keyloggers, or social engineering.
Two‑step authentication introduces a critical second barrier. Even if a hacker obtains your password, they can’t proceed without the second step. That second step—whether it’s a one‑time code, a push notification, or a fingerprint—halts most unauthorized login attempts in their tracks.
It also reduces the effectiveness of common threats like phishing. A fake login form might capture your password, but if you use app‑based or biometric authentication, the attacker hits a wall when they can’t verify the second credential.
Relevance in Email Security and Account Safety
Email is often the primary recovery method for nearly every other account—banking, social media, business systems. If a hacker gains access to your email, they can reset passwords, intercept verification codes, and impersonate you to others.
That’s why enabling two‑step authentication on your email account is one of the most important security actions you can take. Without it, your entire online identity rests on a single password.
Combine this with other security practices like DKIM verification, email spoofing protection, and strong spam filters, and you drastically reduce your risk profile.
How Two‑Step Authentication Works—Step by Step
Primary Factor—Password Entry
The first step in two‑step authentication is typically entering your password. This is the traditional credential—something you know. It’s checked against stored records to confirm your identity.
If this step fails, the system blocks access immediately. If it succeeds, you’re prompted for the second factor. The password remains necessary but insufficient on its own.
Security experts recommend using long, complex passwords that avoid dictionary words or predictable sequences. Password managers like Bitwarden or 1Password can help you generate and store unique passwords for every account.
Secondary Factor—One‑Time Codes, Biometrics, Hardware Keys
The second step introduces an independent method of verification. Common examples include:
- One-time codes sent via SMS or email (less secure, but common).
- App-generated codes using TOTP (Time-based One-Time Password), as seen in apps like Google Authenticator or Authy.
- Push notifications requiring approval (e.g., Duo Mobile, Microsoft Authenticator).
- Biometric scans like fingerprint or facial recognition.
- Physical security keys that use protocols like FIDO2 or U2F (e.g., YubiKey).
Each method adds its own security benefits. TOTP apps are resistant to SIM swapping, while physical keys are immune to phishing. Biometric options offer convenience but may not always be available on all devices.
No matter the form, the key idea is this: the second factor must be tied to you, not just your knowledge. It acts as proof that you—not just someone with your password—are attempting to log in.
How It Integrates with Email-Based Security
Securing Verification Email and Email Encryption Processes
Many platforms use email as a fallback for two‑step verification codes or password resets. If your email account is compromised, attackers can hijack every other service linked to it. That’s why securing email access is fundamental.
Two‑step authentication adds critical resilience here. It ensures that even if your verification emails are intercepted or faked, access isn’t granted without the second factor.
This ties directly into email encryption, which protects message content, and verification systems that ensure only authorized users can confirm identities through trusted channels.
Combining encrypted communications with two‑step authentication creates a robust foundation for secure digital correspondence.
Complementing DKIM and Protection from Email Spoofing
While two‑step authentication doesn’t directly prevent spoofed emails from reaching your inbox, it complements tools like DKIM that verify sender identity. DKIM ensures the message comes from an authorized domain, while two‑step ensures that only legitimate users access that account in the first place.
Similarly, email spoofing is often used in phishing attacks designed to steal passwords. Two‑step authentication acts as a safety net—even if a password is stolen, the attacker can’t use it.
Together, these tools form a multi-layered defense that mitigates everything from fake emails to unauthorized access and impersonation attempts.
Setting Up Two‑Step Authentication on Popular Platforms
Email Providers and Banking Platforms
Most major services offer two‑step authentication, but the setup process varies slightly between platforms. For email providers like Gmail, Outlook, and Yahoo, the option is typically found under “Security Settings” or “Account Settings.” Once enabled, you can choose from options like app-based authentication, SMS codes, or backup email addresses.
For business or enterprise accounts managed by IT admins, two‑step authentication can be enforced company-wide through policy controls. Platforms like Microsoft 365 and Google Workspace support this via centralized dashboards, where admins can view compliance and prompt users to activate the feature.
Banking platforms often include two-step verification by default for high-risk transactions, like transferring funds or changing account settings. In such cases, a code sent via SMS or mobile app is required in addition to your login credentials. While convenient, SMS is vulnerable to SIM-swapping attacks, which is why many platforms now encourage users to move to app-based or hardware key authentication.
Tips for Backup Methods and Recovery
One common hesitation with two‑step authentication is the question, “What if I lose access to my phone or second factor?” That’s where backup methods come in. Most platforms offer one or more of the following:
- Backup codes: A set of one-time use codes you can print or store offline.
- Secondary email address: A fallback for recovery messages.
- Trusted devices: Previously verified devices that can bypass the second step.
- Security questions: Less common now due to security concerns, but still in use.
It’s critical to set up at least one backup method when enabling two-step authentication. This ensures that you won’t be locked out if your main device is lost, stolen, or reset. Avoid using methods like SMS-only verification as your sole recovery option, especially for high-value accounts like email and banking.
Best Practices for Using Two‑Step Authentication Safely
Choosing the Right Secondary Factor
Not all second factors offer the same level of security. While SMS-based codes are better than nothing, they are vulnerable to interception and SIM-swapping. App-based authenticators (like Google Authenticator, Authy, or Microsoft Authenticator) are much more secure and offer offline access.
For users managing sensitive data or business assets, hardware tokens like YubiKey offer top-tier protection. These keys support open standards like FIDO2 and provide unphishable authentication.
When choosing your secondary factor, consider both security and usability. While biometrics and push notifications offer convenience, they must also be tied to secure and updated devices.
Avoiding Common Pitfalls and Recovery Headaches
Users sometimes disable two‑step authentication because they forget to set up backup methods or lose their devices. This can be avoided with a few simple habits:
- Always save your backup codes in a secure, offline location.
- Avoid registering untrusted public devices.
- Regularly test your recovery options.
- Use password managers that support storing 2FA backups or codes.
Treat your second factor with the same care as your password. Never share your codes, store them in plain text, or reuse authentication settings across unrelated platforms.
Addressing Misconceptions and Troubleshooting
What If My Phone Is Lost?
Losing access to your second factor is inconvenient, but it doesn’t have to be a disaster. If you’ve saved backup codes or enabled a secondary email, you can recover access relatively easily. Most platforms also offer identity verification processes—though time-consuming—that allow you to prove ownership of your account.
In some cases, IT support or system admins can reset authentication for enterprise-managed accounts. This is why businesses should document internal recovery workflows and maintain secure records of employee device configurations.
Concerns About Usability vs. Security
A common argument against two‑step authentication is that it adds friction to the login process. While that’s true, the added step is minor compared to the consequences of a data breach. A few extra seconds during login is a small price to pay for vastly improved security.
Many platforms offer ways to “remember” trusted devices, reducing the need for constant verification while maintaining protection from unknown or new devices. The goal isn’t to make access difficult—it’s to ensure the person logging in is actually you.
Regulatory and Privacy Considerations
GDPR Requirements for Stored Authentication Data
Under GDPR, organizations must protect personal data—including login credentials and authentication factors. This includes ensuring that second-factor credentials (such as biometric templates or phone numbers) are stored securely and only used for their intended purpose.
Data processors must also ensure that authentication logs do not expose unnecessary personal information and that recovery methods comply with consent and transparency requirements.
For businesses operating in the EU or handling EU citizen data, enforcing strong authentication—while respecting privacy rules—is part of maintaining regulatory compliance.
Enterprise Enforcement Policies
Many companies now mandate two‑step authentication for internal tools, cloud services, and remote access systems. This is often enforced via Single Sign-On (SSO) platforms that integrate multi-factor authentication (MFA) directly into the login workflow.
Employees are typically required to use approved apps or devices and may be restricted from disabling 2FA without administrative override. These policies help reduce attack surfaces in large organizations and are often part of broader cybersecurity and compliance strategies.
How Two‑Step Authentication Fits into Broader Cybersecurity Strategy
Integrating with Email Encryption, DKIM, and Anti‑Spoofing Measures
Two‑step authentication works best when used in tandem with other email and account protections. It’s not a standalone fix—but a critical part of a layered defense model.
Consider the role of DKIM in validating email sender identity, or email spoofing protections that block forged messages. Add in email encryption to protect message content, and you begin to build a system where identity, access, and content are all secured independently.
Together, these tools reduce the likelihood of successful phishing, identity theft, or unauthorized access—even if one layer fails.
Supporting a Multi‑Layered Defense Posture
Cybersecurity isn’t about perfect walls—it’s about layered defenses. Two‑step authentication fills a vital role as a second wall against account compromise. When paired with strong passwords, security awareness training, regular patching, and access controls, it forms part of an ecosystem that guards against evolving threats.
As businesses move more operations online—especially with remote teams and SaaS applications—the need for multi-layered defenses grows. Two‑step authentication is no longer just “nice to have”—it’s a minimum standard.
Future Trends in Authentication
Passwordless Logins and Biometric Push
Looking ahead, the security industry is shifting toward passwordless authentication. Systems using biometric scans, device-level authentication, and behavioral patterns are becoming more common. These offer both improved security and better usability.
Two‑step authentication is already evolving to support these methods. Instead of passwords plus codes, we may soon see logins based solely on secure device identity plus biometrics.
Hardware Passkeys and FIDO Standards
The FIDO Alliance has been a key driver of passwordless and phishing-resistant authentication. FIDO2 and WebAuthn standards allow for secure logins using physical devices like YubiKeys or built-in platform authenticators on smartphones.
These hardware-based credentials are cryptographically tied to your device and domain, making them incredibly difficult to intercept or replicate. Major platforms—including Google, Apple, and Microsoft—are adopting passkey support, signaling a broader shift away from traditional credentials.
Conclusion
Two‑step authentication is one of the most effective, accessible, and widely supported tools for protecting your digital identity. Whether you’re a business owner managing financial systems, an email user wanting better protection, or an IT team enforcing policy, the value is the same: keep unauthorized users out.
Its strength lies in its simplicity. By requiring not just what you know, but what you have, two‑step authentication neutralizes a wide range of common cyber threats. Combined with technologies like DKIM, encryption, and anti‑spoofing, it forms a core pillar of digital security in 2025 and beyond.
FAQs
Is two‑step authentication the same as two‑factor authentication?
Not exactly. Two‑factor authentication requires two distinct types of credentials, while two‑step may use two of the same type. However, both offer strong layered security.
Can 2FA prevent phishing?
It can greatly reduce the risk. Even if a password is stolen via phishing, 2FA blocks access unless the attacker also has your second factor.
What happens if I lose access to my second factor?
Use your backup codes, recovery email, or trusted devices. If those aren’t available, contact the service provider’s support for recovery options.
Does 2FA really block email spoofing?
Not directly, but it complements systems like DKIM that validate sender identity. 2FA ensures only legitimate users access email accounts, reducing abuse.
Can GDPR affect my use of 2FA?
Yes. GDPR requires organizations to protect authentication data and ensure users understand how their credentials are used and stored.