A DMARC record is one of the most important tools you can use to protect your domain from email spoofing and phishing. It works behind the scenes to tell email providers how to handle messages that fail authentication checks like SPF and DKIM.
So, what does that actually mean for you? Simply put: DMARC helps make sure that only legitimate senders can use your domain—and blocks the bad guys.
In this post, we’ll walk you through what a DMARC record is, why it matters, how to set it up, and the clear benefits it brings to your email security.
Let’s take the mystery out of DMARC, step by step.
What Is a DMARC Record? Definition and Purpose
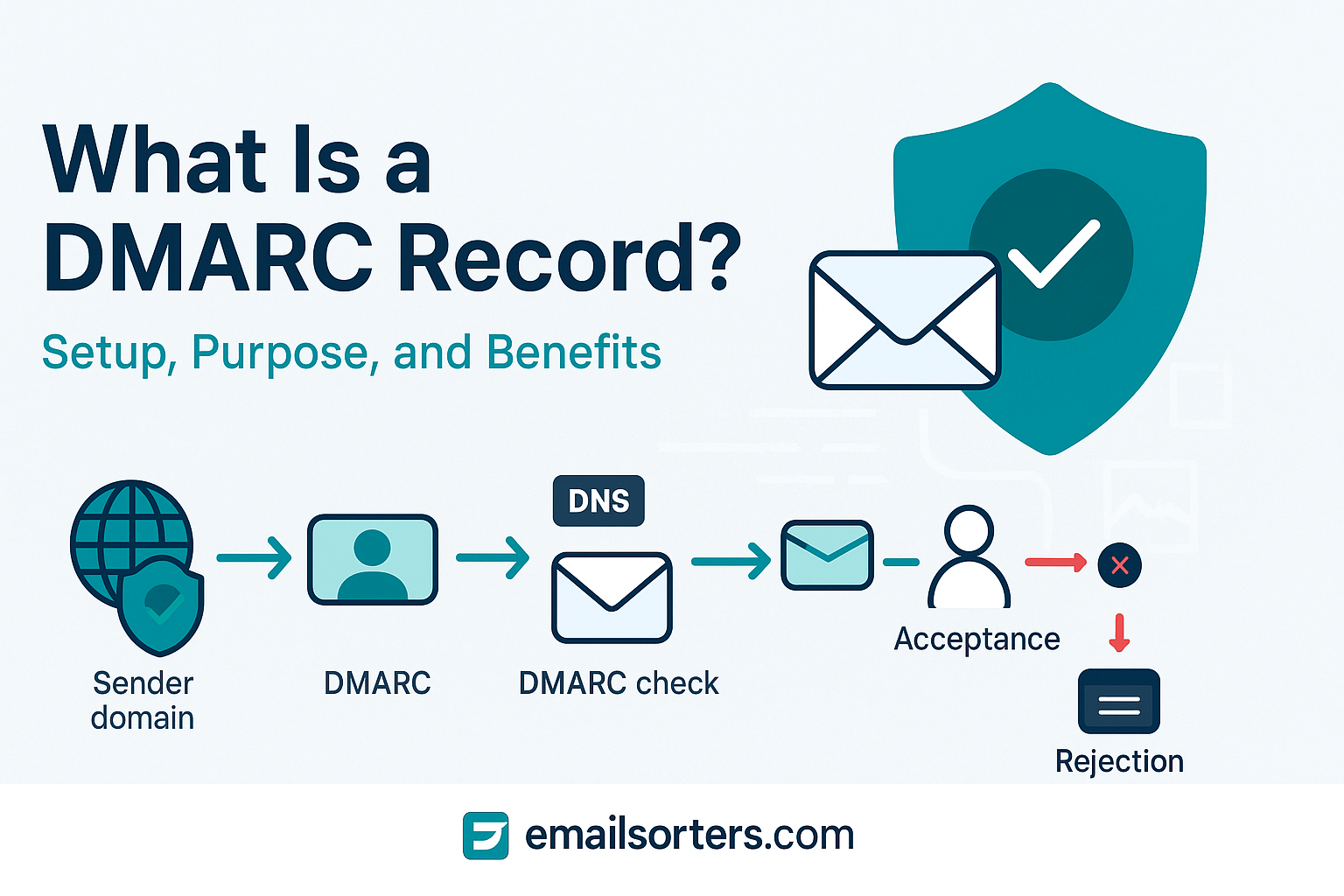
A DMARC record is a DNS TXT entry containing instructions about how recipient mail servers should handle emails that fail SPF and DKIM checks. It tells receiving servers whether to accept, quarantine, or reject messages claiming to be from your domain. DMARC also specifies where to send reports of authentication failures, allowing domain owners to monitor misuse and adjust policies accordingly.
The purpose of DMARC is twofold: protect your domain against spoofing and provide feedback on unauthorized email activity. Without it, attackers can impersonate your domain easily, potentially misleading recipients, damaging your brand, and increasing spam or phishing campaigns. With DMARC in place, you gain insight into who’s sending email in your name and ensure your domain is used only in trusted contexts.
How DMARC Works in Email Authentication
DMARC sits on top of SPF and DKIM, tying them together by checking that at least one validation passes and that the “From:” header aligns with your domain. The protocol has three main actions: none (monitoring only), quarantine (treat as suspicious), or reject (block outright). When a receiver gets an email, it checks the SPF and DKIM records, verifies alignment with the domain in the “From” field, and applies the DMARC policy.
This mechanism reduces the risk of email spoofing and enhances deliverability for legitimate messages. It also generates aggregate and forensic reports, giving domain owners visibility into how their email infrastructure performs and whether unauthorized servers are trying to send on their behalf.
Why DMARC Matters for Marketers and IT Admins
A properly configured DMARC policy signals to mailbox providers like Gmail, Outlook, and Yahoo that your domain is secure and managed systematically. This reputation-building improves deliverability, reducing the chance that genuine marketing messages are sent to spam folders.
It also strengthens brand perception. Consumers who verify your domain via DMARC trust your emails more, knowing they’re authentic. In industries like finance or healthcare, where email triage is critical, DMARC can be a competitive differentiator.
Mitigating Email Spoofing and Phishing Abuse
Email spoofing—when malicious actors impersonate your domain—is a significant threat. It can lead to phishing attacks where recipients are tricked into clicking links, sharing personal data, or executing fraudulent payments. DMARC blocks these messages outright when rejection policies are in place, protecting recipients and preserving your domain’s integrity.
Using DMARC also helps maintain compliance with anti-phishing best practices. For regulated industries, demonstrating active domain protection through DMARC analytics can be a valuable compliance metric.
Essential Components of a DMARC Record
A DMARC record consists of several tag/value pairs that define policy and reporting:
v=: Always set to DMARC1.p=: Specifies the policy action (none,quarantine, orreject).rua=: URI(s) for receiving aggregate reports in XML form.ruf=: (Optional) URI(s) for forensic reports.fo=: Determines forensic reporting options.pct=: Percentage of mail to which the policy applies (e.g., start with 10%).adkim=andaspf=: Define alignment strictness for DKIM and SPF.
A simple monitoring entry looks like:
iniCopyv=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; pct=100
A hardened reject policy might be:
iniCopyv=DMARC1; p=reject; rua=mailto:dmarc-agg@yourdomain.com; ruf=mailto:dmarc-forensic@yourdomain.com; pct=100; adkim=s; aspf=s; fo=1
These configurations ensure that recipient domains know how strictly to enforce email authentication and where to send valuable reporting data for future analysis.
How to Set Up a DMARC Record—Step by Step
Setting up DMARC involves four strategic steps:
- Ensure SPF and DKIM are in Place
You can’t enforce DMARC without first configuring SPF and DKIM records correctly. These protocols verify the sender’s identity and sign outgoing emails. Once those are validated and in use, DMARC provides effective enforcement. - Create a Suggested DMARC DNS Record
Start with a monitoring policy (p=none) to collect data before enforcing quarantines or rejections: makefileCopyName: _dmarc.yourdomain.com Type: TXT Value: v=DMARC1; p=none; rua=mailto:dmarc@yourdomain.com; pct=100 - Publish the Record in Your DNS Zone
Log into your DNS provider (e.g., GoDaddy, Cloudflare, AWS Route 53), navigate to DNS management, and add the TXT record under the hostname_dmarc. - Review Reports and Adjust Policy Gradually
Parse aggregate (RUA) data to identify legitimate and fraudulent senders. Start enforcing quarantine at 25–50%, and check that delivery remains smooth. Incrementally move to 100% quarantine or reject, ensuring reliable enforcement against abuse.
Once you’re confident legitimate email won’t be harmed, finalize the policy with p=reject. This blocks spoofed messages but requires careful review to avoid harming email flow during migration or system changes.
DMARC Reporting and How to Interpret Reports
One of the key benefits of DMARC is its reporting feature, which gives domain owners visibility into how their domain is used—or abused. There are two types of reports:
- Aggregate Reports (RUA): Sent daily by participating mail servers, these XML reports summarize authentication results for all emails claiming your domain. They provide data on how many messages passed or failed SPF/DKIM checks, sources of sending, and potential misalignments.
- Forensic Reports (RUF): These are detailed incident reports sent in near real-time when an authentication failure occurs. They contain message samples or header data to help diagnose spoofing attempts.
Understanding these reports can be challenging but essential for effective DMARC management. There are several free and commercial DMARC report analyzers that parse XML into human-readable dashboards, highlighting legitimate vs. fraudulent sources and helping refine your policies.
Common Challenges When Implementing DMARC
Implementing DMARC is not always straightforward. Many organizations face issues such as:
- Misalignment: Emails failing because the domain in the “From” header doesn’t align with SPF or DKIM domains.
- Third-party Senders: Services like marketing platforms or CRMs may send emails on your behalf but require special DKIM/SPF setups to pass authentication.
- Complex DNS Management: Adding and managing records in different DNS systems can be confusing.
- Interpreting Reports: Volume and technical format of reports may overwhelm small teams without dedicated email security resources.
Overcoming these challenges requires careful planning, testing, and collaboration with your IT and marketing teams. Documenting your email ecosystem and regularly auditing your DNS records are key to successful DMARC deployment.
How DMARC Complements SPF and DKIM
SPF (Sender Policy Framework) and DKIM form the foundation of email authentication. SPF specifies which IP addresses are authorized to send mail on behalf of your domain, while DKIM adds cryptographic signatures to prove the message’s integrity.
DMARC ties these together by:
- Checking that either SPF or DKIM passes authentication.
- Verifying that the domains used in SPF or DKIM align with the domain in the “From” header.
- Giving domain owners control over the treatment of unauthenticated mail.
Without DMARC, SPF and DKIM work independently and don’t guarantee protection against spoofing. DMARC enforces the alignment and creates accountability.
Benefits of DMARC Beyond Security
While DMARC’s primary function is preventing spoofing and phishing, its benefits extend further:
- Improved Deliverability: Mailbox providers prefer domains with DMARC, leading to better inbox placement.
- Visibility: Insight into your email ecosystem, including authorized senders and third-party services.
- Brand Protection: Prevents impersonation that can erode customer trust and damage reputation.
- Regulatory Compliance: Assists with data protection and anti-fraud mandates by controlling how your domain is used.
Incorporating DMARC as part of a wider email security framework—alongside email security, encryption, and anti-spoofing measures—enhances your overall posture.
External Resources and Further Reading
For an authoritative overview, see the Wikipedia entry on DMARC. It provides technical details and a history of the protocol’s development.
Industry leaders like Forbes have highlighted DMARC as a vital component of business email security. Their coverage reinforces the importance of proactive domain protection amid rising phishing attacks.
Conclusion
A DMARC record is a critical element for anyone serious about email security and domain reputation management. By enforcing authentication, providing visibility into email traffic, and offering control over unauthorized usage, DMARC protects your brand and your recipients.
Whether you’re an IT admin securing enterprise domains or a marketer ensuring message deliverability, DMARC’s setup and ongoing management are foundational to safe and trusted email communication in 2025 and beyond.
Implement DMARC alongside complementary technologies like SPF, DKIM, and robust email security practices to build a resilient, trustworthy email environment.
FAQs
What happens if I don’t have a DMARC record?
Without DMARC, your domain is vulnerable to spoofing and phishing attacks, and you have no visibility into unauthorized email use. Your emails may also have lower deliverability.
Can DMARC cause legitimate emails to be rejected?
Yes, if SPF or DKIM aren’t properly configured or aligned with your sending domains, legitimate emails may fail DMARC checks and be rejected or quarantined.
How long does it take for a DMARC record to take effect?
DNS propagation can take up to 48 hours, but most changes are effective within a few hours.
Is DMARC setup complex for small businesses?
While technical, many DNS providers and email platforms offer guides and tools to simplify setup. Starting with a monitoring policy (p=none) helps ease implementation.
Does DMARC protect against all email threats?
No single technology is foolproof. DMARC protects mainly against domain spoofing. It should be part of a multi-layered email security strategy including encryption, user education, and spam filtering.