Reverse DNS lookup might sound technical, but it plays a key role in how email servers and networks verify who you are.
Instead of translating a domain name into an IP address (like regular DNS), reverse DNS does the opposite, it checks the IP address to see which domain it belongs to. This small step adds a big layer of trust, especially in email delivery and spam prevention.
In this post, we’ll break down how reverse DNS lookup works, why it matters for email senders and businesses, and how to set it up the right way.
Let’s clear up the mystery behind reverse DNS, once and for all.
What Is Reverse DNS Lookup?
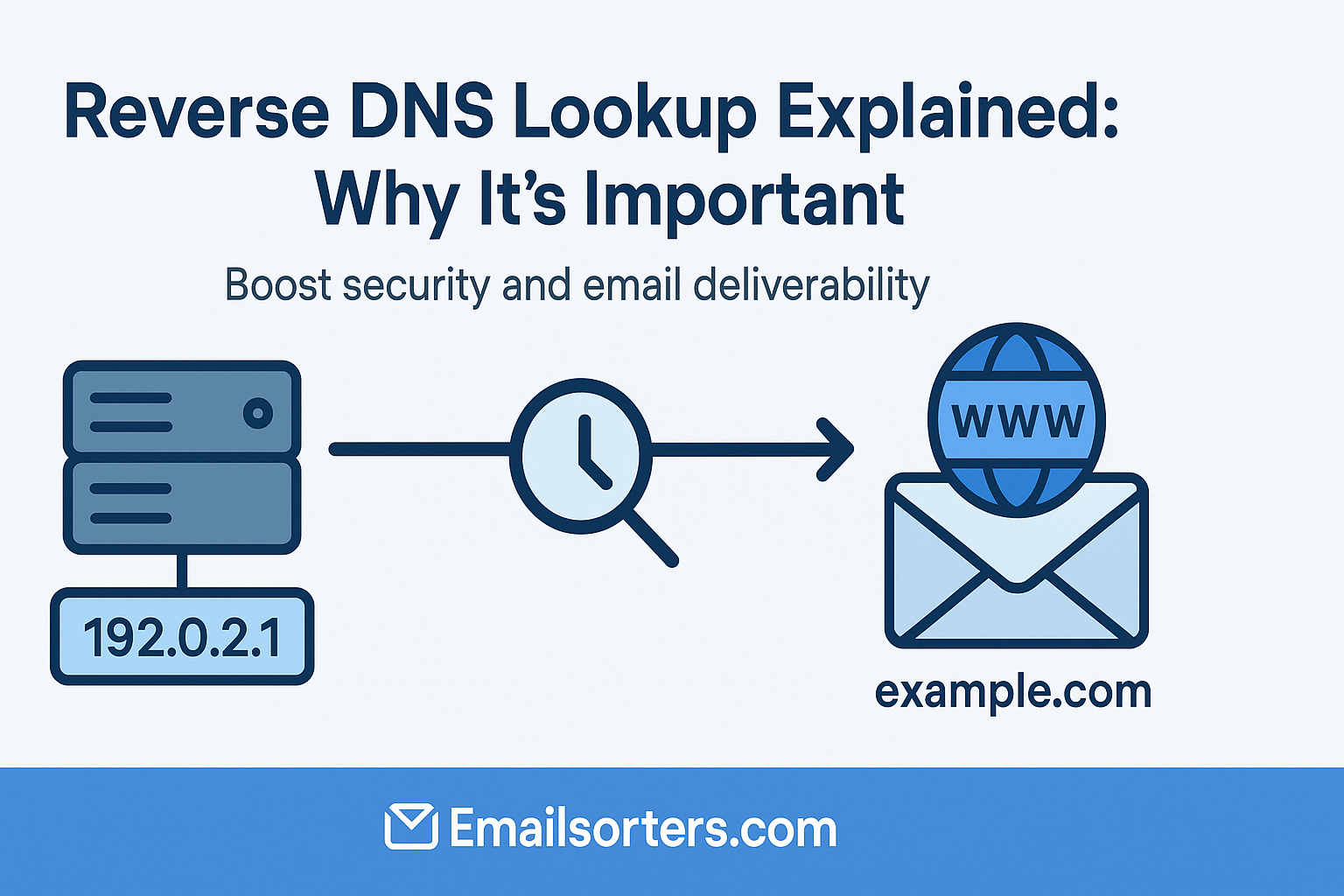
Reverse DNS lookup (rDNS) is the process of matching an IP address back to a domain name, basically the opposite of a standard DNS lookup.
While a regular DNS turns a domain like example.com into an IP address (so your browser knows where to go), reverse DNS takes that IP and checks what domain it belongs to.
It’s mostly used by email servers and network tools to verify identity, reduce spam, and improve email deliverability. If the IP address of a sender doesn’t match a domain via reverse DNS, it can raise red flags or even land emails in the spam folder.
Difference Between Forward and Reverse DNS
To understand reverse DNS, it’s helpful to first compare it to forward DNS. Forward DNS is the more familiar of the two—it’s what happens when you type “example.com” into a browser and get routed to an IP address like 192.0.2.1. This process is essential for navigating the internet by human-friendly names rather than numerical IPs.
Reverse DNS, on the other hand, performs the opposite function. It takes an IP address and attempts to resolve it to a hostname. This is especially useful for servers, where validating the source of incoming traffic is necessary for security and trust.
Forward DNS uses “A” records (address records), while reverse DNS uses “PTR” (pointer) records. The PTR record exists in a special DNS zone called in-addr.arpa for IPv4 or ip6.arpa for IPv6, and it links an IP to a hostname.
The distinction is fundamental because while anyone can set forward DNS for their domain, setting up reverse DNS requires control over the IP address, typically through coordination with your hosting provider or ISP.
How Reverse DNS Resolution Works Technically
When a server attempts to perform a reverse DNS lookup, it queries the DNS system starting from the root servers, then into the in-addr.arpa domain for IPv4 addresses or ip6.arpa for IPv6. If a PTR record is present for the queried IP, the DNS resolver returns the associated hostname.
For example, a lookup on IP 192.0.2.1 would query 1.2.0.192.in-addr.arpa. If the PTR record is correctly configured, it might return mail.example.com.
This hostname can then be checked against the original sending domain for consistency. When used in conjunction with forward-confirmed reverse DNS (FCrDNS), where the reverse lookup matches the forward DNS for that hostname, the trustworthiness of the connection is considered strong.
This lookup step occurs quietly behind the scenes in many systems, particularly mail servers and security appliances, and is a key criterion in scoring sender reputation.
Why Reverse DNS Is Critical for Email Systems
Reverse DNS (rDNS) is more than just a technical detail; it’s a key trust signal in email communication. When your mail server sends an email, the receiving server often performs a reverse DNS lookup to verify that the IP address matches your domain name. If it doesn’t, that email might be flagged as suspicious or rejected altogether.
Authenticity and Trust Signals in Email Delivery
Email servers often perform rDNS checks as part of their validation process. When an email is received, the server checks the sender’s IP address and performs a reverse DNS lookup to see what domain it resolves to. If the PTR record is missing or the result doesn’t align with the domain sending the message, this can raise a red flag.
Many receiving servers will flag or even outright reject email from IP addresses without a properly configured reverse DNS entry. This is because lacking rDNS is a common trait of compromised machines or misconfigured systems often used in spam or phishing attacks.
In the world of email marketing and enterprise communication, this matters deeply. An email server lacking reverse DNS is essentially anonymous to the receiving server—and anonymity on the internet is rarely trusted. A proper rDNS record serves as a digital handshake, affirming the legitimacy of your mail server.
Impact on Spam Filters and Deliverability
Spam filters don’t just evaluate email content—they scrutinize technical headers and connection details. Reverse DNS is one such detail, and a missing or mismatched PTR record can heavily influence a spam filter’s decision.
Many ISPs and enterprise filters assign points to potential spam indicators. If your mail server lacks reverse DNS, it might get flagged as suspicious, affecting overall deliverability. Some systems outright deny emails from non-resolving IPs, bouncing them back or silently dropping them.
This is especially important for high-volume senders. If your marketing emails are being sent through an IP without proper rDNS, your campaigns may not be reaching their intended audience—costing you open rates, conversions, and brand trust.
For a deeper understanding of how this fits into the broader email infrastructure, review how a SMTP server functions and why it’s essential in email routing and delivery.
Setting Up Reverse DNS for Mail Servers
Setting up reverse DNS (rDNS) for your mail server is a critical step to ensure your emails land in inboxes—not spam folders. Here’s how to do it, step by step:
1. Use a Dedicated IP Address
To configure rDNS, you need control over your mail server’s IP. This is usually a static, dedicated IP, not a shared one.
2. Understand Who Controls Your IP
You can’t set rDNS yourself unless you manage the IP address directly. Typically, your hosting provider or ISP controls it. You’ll need to contact them or access their DNS management panel.
3. Create a PTR Record
Ask your provider to set up a PTR (Pointer) record, which maps your mail server’s IP address to its domain name (like mail.yourdomain.com).
Example:
CopyEdit123.45.67.89 → mail.yourdomain.com
Make sure this domain has a valid A record pointing back to the IP to complete the loop (forward-confirmed rDNS).
4. Match Your Reverse and Forward DNS
Ensure your PTR record and A record match. This alignment boosts trust with email providers and helps pass spam checks.
5. Test Your Setup
Use tools like:
dig -x your.ip.address- Online tools (MXToolbox, DNSstuff)
Check if the PTR record is visible and points to the correct domain.
Role of SMTP Servers and Reverse DNS Validation
SMTP servers are the backbone of email delivery. When your server connects to another server to deliver a message, it shares its IP address as part of the SMTP handshake. That receiving server may then perform a reverse DNS lookup on your IP to validate your identity.
If your IP resolves to a hostname that doesn’t reflect your domain or worse, doesn’t resolve at all, you’re likely to face deliverability issues. This is why most professional SMTP services and ESPs ensure that their IPs have correctly configured reverse DNS records aligned with client domains.
It’s not just about passing a single check—it’s about reducing friction throughout the delivery chain. When reverse DNS aligns with your SPF and DKIM records, the overall trustworthiness of your email system increases significantly.
Steps to Configure Reverse DNS Properly
To set up reverse DNS, you typically need to contact your hosting provider or ISP, as they control the PTR records for the IP addresses they assign. You’ll need to provide the fully qualified domain name (FQDN) you want associated with your IP.
Once configured, test it using tools like dig, nslookup, or web-based DNS checkers. You want your IP to return a hostname, and ideally, that hostname should forward-resolve back to the same IP—this is known as forward-confirmed reverse DNS (FCrDNS), and it’s a strong indicator of authenticity.
This setup should align with your MX record configuration to ensure consistency across DNS entries. Discrepancies between MX records and PTR records can confuse filters and lead to failed message delivery.
How ISPs and Spam Filters Use rDNS Checks
Internet Service Providers (ISPs) and spam filtering systems use a complex set of criteria to determine whether an incoming message is trustworthy. One of the foundational checks in this process is the reverse DNS (rDNS) lookup. When an email is received, the ISP queries the PTR record for the sending IP to verify its legitimacy.
If the rDNS entry either doesn’t exist or does not align with the sender’s domain or hostname, this can trigger suspicion. ISPs consider this a potential sign of spam or malicious activity, especially when coupled with poor domain reputation or missing authentication protocols like SPF, DKIM, or DMARC.
Some mail servers outright reject emails lacking valid rDNS entries, regardless of content. Others may mark them as “suspect,” reducing their inbox placement and damaging your reputation score over time. In both cases, the result is degraded deliverability and compromised sender integrity.
This check becomes even more important for bulk senders, who are often under stricter scrutiny. Whether you’re a transactional email provider or an internal mail relay for a corporation, maintaining an accurate and aligned rDNS entry is non-negotiable for protecting your reputation and ensuring reliable delivery.
Email Blacklisting and Misconfigured Reverse DNS
Misconfigured or absent reverse DNS is a common trigger for blacklisting. When spam filters and ISPs detect repeated instances of non-compliant sending behavior—especially from unauthenticated sources—those IP addresses or domains are added to blacklists used by mail servers worldwide.
These blacklists are referenced by receiving systems to decide whether to accept, flag, or reject incoming mail. Once you’re on a blacklist, your messages may bounce, be silently dropped, or be routed to spam folders.
Most blacklist operators and spam prevention services consider a valid rDNS record one of the basic requirements for removal or avoidance. If your IP fails to resolve to a legitimate hostname—or worse, resolves to a generic or ISP-owned placeholder—it’s viewed as a red flag.
To stay off these lists, follow best practices and regularly monitor your IP’s status. You can also read our detailed guide on Email Blacklisting — Explained: Causes and How to Avoid It for a deeper look at blacklist dynamics.
Troubleshooting Reverse DNS Issues
Even when reverse DNS (rDNS) is configured, issues can still arise and negatively affect your email deliverability. One of the most common problems is the absence of a PTR record. If there’s no PTR record associated with your IP address, email servers may reject your messages or mark them as spam. To fix this, contact your hosting provider or ISP and request that a PTR record be created that maps your IP to a fully qualified domain name (FQDN), like mail.yourdomain.com.
Another frequent issue is a mismatch between the PTR record and the A record. In a healthy setup, your PTR record should resolve your IP address to a domain name, and that domain name should, in turn, resolve back to the same IP via an A record. If the two don’t match, it can trigger warnings or blocks by spam filters. Make sure both records point to each other correctly.
Common Misconfigurations and Their Effects
Several issues can arise during or after setting up reverse DNS. The most common is simply having no PTR record at all. This usually occurs when the ISP or hosting provider hasn’t configured the reverse DNS zone or the record has been deleted.
Another frequent issue is mismatch—where the PTR record returns a hostname, but that hostname doesn’t resolve back to the original IP. This lack of symmetry (forward-confirmed rDNS failure) can lead to trust issues in email validation.
Additionally, some administrators configure a PTR record that points to a hostname different from the domain used in their SMTP HELO command. While not always fatal, this inconsistency can trip up strict spam filters or compliance checks.
A misconfigured rDNS may result in slower delivery, message rejections, or the inability to connect with recipient servers altogether. If you start seeing more bounce-backs or delays, rDNS should be one of the first things you check.
How to Read and Interpret Non-Delivery Reports
When rDNS fails, the effects often appear in the form of non-delivery reports (NDRs), also known as bounce-back messages. These messages typically include SMTP response codes such as 550 or 554, which indicate delivery failure.
If the NDR contains a message like “Reverse DNS failed,” “PTR record not found,” or “Client host rejected: not logged in,” this signals a reverse DNS or authentication issue. Some servers may even include a link to the specific policy that triggered the rejection.
Understanding these NDRs is essential for fixing configuration issues quickly. They often point directly to the problem, whether it’s a missing PTR record, a hostname mismatch, or a broader authentication failure.
You can learn more about these diagnostics in our comprehensive guide on Non-Delivery Reports — Definition and How to Troubleshoot.
Reverse DNS and MX Records: The Alignment Factor
When it comes to email deliverability, reverse DNS and MX records may seem like separate parts of the system—but together, they play a key role in establishing domain credibility and trust. Their alignment can be the difference between your email landing in the inbox or vanishing into spam.
Reverse DNS (rDNS) allows the receiving mail server to look up the domain name that corresponds to the IP address sending the email. MX records, on the other hand, specify which servers are authorized to receive email on behalf of your domain. While they serve different purposes, both point back to one critical factor: domain identity.
If your domain’s MX record points to mail.yourdomain.com, and the sending server’s IP has a PTR (reverse DNS) that also resolves to mail.yourdomain.com, it creates a clean, consistent identity path. This kind of alignment helps mail providers like Gmail or Outlook trust that the sender is legitimate, especially when it’s backed up by SPF, DKIM, and DMARC records.
However, if your rDNS points to a generic ISP hostname or a mismatched domain, and your MX record says something else, it introduces doubt—and doubt leads to spam filtering or outright rejection.
MX Record Configuration in Relation to rDNS
Your mail exchange (MX) records define where incoming mail should be delivered, while reverse DNS tells other mail servers who you are when sending. These two records don’t perform the same function, but aligning them ensures consistency and reduces suspicion.
For example, if your outgoing IP resolves to mail.example.com via PTR, and your MX record also points to mail.example.com, this coherence signals that your domain is properly configured. Disparities between MX and rDNS entries can be seen as misalignment and degrade your credibility with receiving mail systems.
While some organizations use different servers for sending and receiving mail, they should still maintain logical consistency in naming conventions and documentation. Many enterprise environments opt to use the same subdomain (e.g., mail.domain.com) for both incoming and outgoing records for this reason.
When setting up or auditing your DNS infrastructure, double-check the hostname used in your MX record and compare it to your rDNS record. If they’re wildly different or unrelated, it might be time to revise.
Ensuring Hostname Consistency Across Records
Consistency is the cornerstone of good email infrastructure. The PTR record should map an IP address to a hostname, and that hostname should in turn resolve to the same IP address—a process known as forward-confirmed reverse DNS (FCrDNS).
Additionally, this hostname should ideally match the HELO/EHLO banner of your SMTP server. Many spam filters compare the SMTP HELO hostname against rDNS and MX data. When these don’t match or resolve inconsistently, your emails risk being rejected or flagged.
Aligning your rDNS with both MX records and HELO identity shows that your system is correctly and transparently configured. This alignment also helps prevent email spoofing and builds a stronger sender reputation across the board.
Preventing Email Spoofing with Reverse DNS
Email spoofing is a common tactic used in phishing and spam attacks—where someone forges the “From” address to make a message look like it’s coming from a trusted source. One of the most effective ways to help prevent spoofing is by setting up reverse DNS (rDNS) correctly.
Reverse DNS doesn’t stop spoofing on its own, but it plays an important role in verifying the identity of the sending server. When an email is received, the recipient’s server often checks whether the sending IP address resolves back to a domain name (via rDNS) and whether that domain name aligns with the rest of the message headers. If the reverse DNS record is missing or points to a generic or unrelated domain, the message is far more likely to be flagged or rejected.
When combined with other email authentication protocols like SPF, DKIM, and DMARC, reverse DNS helps create a trustworthy sender profile. For example, if your rDNS points to mail.yourdomain.com, and your SPF record authorizes that domain’s IP, the receiving server can cross-verify those signals. This layered approach makes it much harder for attackers to impersonate your domain.
How rDNS Helps Mitigate Spoofing Risks
Email spoofing occurs when attackers forge the “From” address in a message header to make it appear as if it was sent from a trusted source. This tactic is commonly used in phishing attacks and can seriously damage the reputation of legitimate senders.
Reverse DNS plays a critical role in preventing spoofing by verifying the IP address of the sending server. When a receiving server performs an rDNS check and the result doesn’t align with the sender’s domain, it raises a red flag that the message may be fraudulent.
Many anti-spam filters use reverse DNS as part of their broader email authentication strategy. If the PTR record for a sending IP does not resolve to a hostname that can be traced back to the sending domain, the email might be rejected or quarantined.
While rDNS alone isn’t enough to stop spoofing, it is a foundational layer of security. In combination with other mechanisms, it adds a robust signal of authenticity that helps protect your domain from being impersonated.
Combining rDNS with SPF, DKIM, and DMARC
To truly prevent spoofing, reverse DNS should be deployed alongside other industry-standard email authentication protocols: SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance).
SPF allows you to specify which IPs are authorized to send mail on your behalf. DKIM adds a digital signature to your messages, which can be verified by recipients. DMARC ties SPF and DKIM together and gives you control over how to handle failed authentication attempts.
Reverse DNS supports these protocols by adding an extra layer of traceability. When all these systems are aligned and configured correctly, your messages become significantly harder to forge—and your domain much less likely to be targeted by spoofers.
This combination not only protects your recipients but also boosts your email delivery rates, helping you avoid being mistaken for a spammer by overzealous filters.
Testing and Verifying Your Reverse DNS Records
Once you’ve set up reverse DNS (rDNS), it’s essential to test and verify that it’s working correctly. A misconfigured or missing rDNS record can lead to email delivery problems—even if everything else is set up properly.
To begin, the most direct way to test rDNS is by using a reverse DNS lookup tool. You can run a simple command from your terminal:
cssCopyEditdig -x [your IP address]
Or, if you’re on Windows, use:
cssCopyEditnslookup [your IP address]
These commands return the domain name associated with your IP address (your PTR record). If no result appears, or the name doesn’t match your mail server’s hostname, your rDNS is likely misconfigured.
You can also use online tools like MXToolbox, DNSstuff, or IntoDNS. These platforms provide quick diagnostics and highlight potential issues with your DNS and email configuration—including rDNS, SPF, DKIM, and DMARC.
Once you confirm your PTR record is in place, the next step is to check for alignment. Make sure the domain name returned by your rDNS lookup has an A record that points back to the same IP. This is called a forward-confirmed reverse DNS (FCrDNS), and it’s a key trust factor for many mail servers.
Additionally, review your mail server logs after sending test messages. Some receiving servers will include reverse DNS results in bounce messages or headers, which can help confirm whether your rDNS is being recognized and trusted.
Verifying rDNS isn’t a one-time task—it should be part of your regular email health checks. Any changes to your hosting, DNS provider, or IP address may require an update to your PTR records.
Tools for Checking Reverse DNS Setup
Once your PTR record is configured, the next step is to test and verify it. Several tools can help with this, both command-line and web-based. Popular methods include using nslookup, dig, or online DNS tools like MXToolbox, DNSChecker.org, and IntoDNS.
For instance, the nslookup command on Windows or Linux allows you to quickly verify reverse DNS:
nginxCopyEditnslookup 192.0.2.1
The result should return a fully qualified domain name (FQDN). You can then perform a forward lookup on that domain to see if it maps back to the original IP, confirming forward-confirmed rDNS (FCrDNS).
These tests should be part of your regular email infrastructure audits, especially after IP changes, DNS migrations, or server reconfigurations.
Interpreting Lookup Results Correctly
When reading rDNS results, look for a valid hostname that matches your organization’s domain. If the hostname returned is a generic ISP address like host-192-0-2-1.isp.com, that’s a red flag for mail receivers. Ideally, the hostname should resemble something like mail.example.com.
Also verify that the hostname resolves forward to the same IP. A mismatch here can damage credibility with spam filters and cause inconsistencies in logs and non-delivery reports.
If the reverse DNS lookup fails entirely (e.g., “Non-existent domain”), then the PTR record is missing or misconfigured. In such cases, reach out to your ISP or hosting provider immediately to request proper setup.
Regular testing ensures that your email infrastructure remains compliant, trusted, and secure.
Reverse DNS in Cloud and Hybrid Infrastructures
Setting up reverse DNS (rDNS) is relatively straightforward on traditional dedicated servers, but things get more complex in cloud and hybrid environments. As more organizations shift to platforms like AWS, Azure, and Google Cloud—or blend on-premise and cloud infrastructure—understanding how rDNS works across these systems becomes essential for maintaining email deliverability and network credibility.
In public cloud platforms, IP addresses are typically owned and managed by the provider—not by you. This means you can’t directly set a PTR (rDNS) record yourself. Instead, cloud providers often require you to submit a request or follow a specific process. For example, AWS requires you to create a reverse DNS request through their support center, and your domain’s A record must already point to the IP before the change is approved. Azure and Google Cloud follow similar procedures. This extra layer of validation helps ensure only legitimate use of reverse DNS and reduces the risk of abuse.
In hybrid environments, where on-premise mail servers might route through cloud-based infrastructure or third-party mail gateways, reverse DNS must be managed carefully. Any external-facing IPs used to send email must have consistent rDNS records that align with your authenticated sending domain. Misalignment between your cloud IPs, mail server hostnames, and DNS records can trigger spam filters and reduce trust.
It’s also important to coordinate rDNS settings with your SPF, DKIM, and DMARC records across both environments. While SPF lists which servers are allowed to send on your behalf, rDNS reinforces those claims by adding identity to the IP addresses behind the scenes.
Challenges with Cloud Mail Services
Cloud-based infrastructure adds complexity to reverse DNS management. Services like Amazon SES, Microsoft Azure, and Google Cloud often use shared IP addresses or delegated blocks, which means the PTR records are controlled by the provider—not you.
While these providers typically configure PTR records for their sending services, they may not match your brand or domain unless explicitly customized. In AWS, for example, you must request a reverse DNS change via support if you’re using a static IP.
This limitation can affect brand alignment and deliverability if left unchecked. Without control over PTR records, your domain may appear generic or mismatched, increasing the chances of being filtered or blacklisted.
Always consult your cloud provider’s documentation to understand how to configure rDNS properly in their environment.
Best Practices for Hybrid Server Configurations
In hybrid setups—where some email traffic is routed through on-prem servers and some through cloud services—consistency becomes paramount. Each IP used for sending must have an accurate and domain-aligned PTR record.
Maintain documentation of all sending IPs and their respective hostnames. When setting up rDNS, ensure each provider (your hosting partner and your cloud vendor) points to hostnames that clearly relate to your domain.
Using subdomains (e.g., smtp1.example.com for on-prem and smtp2.example.com for cloud) helps differentiate and validate each sending source. These should be reflected consistently in your SPF, DKIM, and DMARC records.
With the right planning, hybrid configurations can still meet all authentication standards and maintain excellent deliverability.
Reverse DNS Beyond Email: Other Use Cases
While reverse DNS (rDNS) is widely known for its role in email authentication and spam prevention, its usefulness goes well beyond email systems. In fact, many networking, security, and analytics tools rely on rDNS to add visibility, context, and control across digital infrastructure.
One common use case is network diagnostics and logging. Tools like traceroute, ping, and firewall logs often use reverse DNS to resolve IP addresses into human-readable domain names. This makes it easier for system administrators and security teams to identify where traffic is coming from, especially when tracking issues across global networks or cloud services.
In cybersecurity, rDNS is often used to help detect suspicious activity. Intrusion detection systems (IDS) and security information and event management (SIEM) platforms may use reverse lookups to classify IPs, identify known hosts, or spot anomalies—like internal systems communicating with domains they normally wouldn’t. It’s also used in blacklists and threat intelligence feeds to help correlate malicious IPs with domains or organizations.
rDNS also plays a role in content filtering and access control. Some systems use domain-based policies to restrict access or route traffic, and rDNS can provide helpful name-based rules when IP-based controls alone are too rigid.
In web analytics and server logs, reverse DNS helps website owners and IT teams understand where their visitors come from. By resolving IPs to hostnames, they can identify ISPs, companies, or regional infrastructure that might otherwise look like anonymous traffic.
Network Forensics and Abuse Detection
While reverse DNS is most visible in email, it also plays a significant role in broader network administration and cybersecurity. In network forensics, reverse DNS helps analysts identify the origin of suspicious or malicious traffic.
By resolving an IP address to a hostname, security teams can trace threats, correlate logs, and better understand attack vectors. For example, identifying that a brute-force login attempt came from a server labeled as vps.compromisedhost.com provides immediate context that wouldn’t be available from just the IP.
Additionally, threat intelligence systems often rely on rDNS data to enrich alerts, filter traffic, and prioritize incident responses.
Role in Secure Web Hosting and Application Services
In web hosting, reverse DNS helps with transparency and diagnostics. When a server initiates a connection—whether for an API call, file transfer, or remote login—the receiving system may log the hostname derived from rDNS for accountability and access control.
Some SSL certificate providers and third-party services use reverse DNS as part of their validation processes. Even search engines occasionally reference PTR data to verify authenticity of crawlers and bots.
While not mandatory for every application, reverse DNS continues to serve as a foundational tool for identifying systems, mitigating abuse, and reinforcing trust across distributed environments.
Real-World Consequences of Poor Reverse DNS Setup
A poorly configured or missing reverse DNS (rDNS) record might seem like a small oversight, but in practice, it can lead to serious consequences—especially when it comes to email deliverability, brand trust, and network visibility.
One of the most immediate impacts is on email delivery. Many receiving mail servers, including those operated by Gmail, Microsoft, and Yahoo, use rDNS as a basic check to verify the legitimacy of the sending IP. If there’s no PTR (reverse DNS) record—or if it points to a mismatched or generic domain—your emails are far more likely to be flagged as spam, delayed, or outright rejected. This can result in lost communication with customers, missed business opportunities, and frustrated recipients.
Beyond email, a poor rDNS setup can also affect your company’s reputation and credibility. For example, when IT teams or partners see logs from your IP and notice a vague or unrelated hostname like 123-45-67-89.isp.com, it reflects a lack of technical oversight. This can raise red flags during audits, security reviews, or partnership evaluations.
Delivery Failures and Email Rejection Examples
Failure to configure reverse DNS properly can have immediate and severe consequences for any organization that relies on email communication. One of the most common outcomes is outright rejection of messages by receiving servers. These rejections typically present as SMTP error codes, such as 550 (“Requested action not taken: mailbox unavailable”) or 554 (“Transaction failed”).
For instance, if your marketing campaign is routed through an IP without a valid PTR record, recipients on platforms like Yahoo, Comcast, or Microsoft may never see your message. Their mail servers often refuse messages from IPs that fail rDNS checks, especially when combined with weak SPF or DKIM records.
In another case, a company using a shared IP from a hosting provider may inherit a PTR record that resolves to a generic ISP hostname. If that hostname has a poor reputation—or if it doesn’t match the domain used in the HELO string—emails may be flagged as spam or silently discarded.
These failures don’t just cost you deliverability—they can impact customer trust, lead to lost revenue, and disrupt internal communications. Consistently monitoring and validating your rDNS setup helps prevent these outcomes.
Security Risks and IP Reputation Damage
Beyond email deliverability, poor reverse DNS configuration can open doors to broader security risks. If your IP lacks a valid PTR record, it may be indistinguishable from those used in botnets, open relays, or other malicious infrastructure. Security systems often treat such IPs as high risk, flagging or blocking them from accessing sensitive networks or APIs.
This tarnished reputation can spread. Blacklists like Spamhaus or Barracuda may list your IP, causing disruptions across email, web hosting, and data exchanges. Once blacklisted, even unrelated services on your infrastructure may suffer reduced performance and reach.
Additionally, a compromised reverse DNS setup could allow for domain spoofing or impersonation if attackers exploit inconsistencies between forward and reverse mappings. This can lead to phishing attacks and brand damage.
Maintaining accurate, consistent rDNS records across all your IP addresses is a foundational element of cyber hygiene. It signals that your systems are properly configured, actively managed, and trustworthy.
Conclusion
Reverse DNS is often treated as a backend technical detail, but its importance in maintaining email deliverability, server credibility, and network security cannot be overstated. Whether you’re running an enterprise SMTP server, managing a cloud-based email system, or optimizing your marketing campaigns, reverse DNS ensures that your IP address communicates trust and authenticity to the internet.
From preventing spoofing and blocking spam to supporting email protocols like SPF, DKIM, and DMARC, reverse DNS acts as a crucial piece of the validation puzzle. And as cyber threats become more sophisticated and email standards continue to evolve, maintaining proper rDNS configuration is no longer optional—it’s essential.
Take the time to audit your reverse DNS records, align them with your MX records and domain settings, and integrate them into a comprehensive email authentication strategy. The payoff is improved deliverability, fewer bounced emails, and a safer, more reliable digital presence.
FAQs
Can I use reverse DNS without owning the IP?
No. Reverse DNS records (PTR) are managed by whoever controls the IP block, typically your ISP or hosting provider. If you don’t own the IP, you must request the PTR record update from them.
How often should I audit my reverse DNS records?
At a minimum, review your rDNS configuration quarterly, and always after making DNS changes, switching ISPs, or launching new servers. Ongoing monitoring helps prevent deliverability issues and misconfigurations.
Is reverse DNS required for all types of servers?
Not necessarily. It’s most critical for email servers, where rDNS affects deliverability and spam filtering. However, it’s beneficial for any publicly exposed service, including web and FTP servers.
What’s the fastest way to check my reverse DNS entry?
Use a command-line tool like nslookup or online tools like MXToolbox. Simply input your IP address and review the PTR record that is returned to verify if it resolves to the correct hostname.
Do reverse DNS mismatches always cause deliverability issues?
Not always, but mismatches raise suspicion with spam filters and can negatively impact reputation. Combined with other weak authentication practices, they increase the likelihood of being flagged or blocked.